Part 1 – Synopsis of New Series
Going into a new series once again around modern device management, and perhaps an area not written about much at all.
Here we will be going into depth in regard to managed devices specifically around the BYOD (Bring your own device)
Whilst there is tremendous convenience of using a BYOD policy the areas of management and security for this can start to get very complex.
This series will start to look at how we can understand the differences and the separations between how we manage corporate devices and also BYOD devices.
The below categories are how we are going to look further into BYOD device management within the new series.
Device Enrolment: Key to BYOD Device Management
The first initial area in this instance will be regarding the device enrolment. The Strategy and planning of how a device would be onboarded or recognized within your M365 environment plays a very important role.
This can derive from using a device enrolment policy, enrolment from a Microsoft Office application as well as going to more explicit grounds of the Enrolment device platform restrictions where we can specifically define which type of enrolment methods we will actually allow.
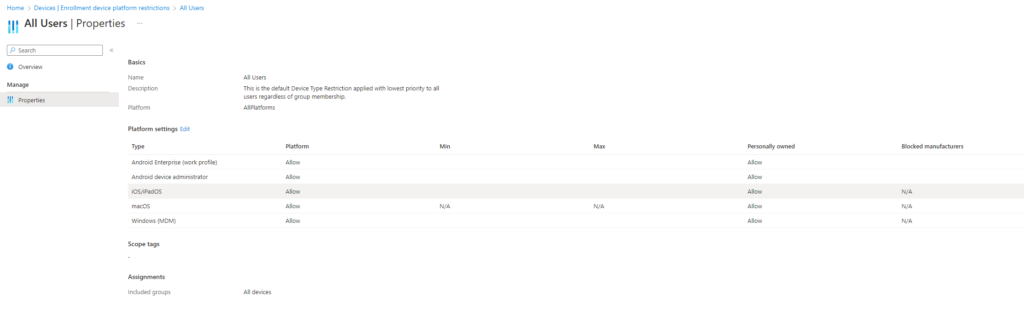
Figure 1.1 – Device enrolment platform restrictions
What we really have to establish on the first basis is that in order for us to manage and handle devices within an organization effectively is that we cannot lump together corporate devices alongside BYOD devices due to the huge gap in the roles that they play within the organization. So very careful planning has to go into the decision-making process on how we move forward.
Compliance/Conditional Access Policies
Another area of focus is we will go into how we will construct conditional access policies. And keeping to the strategy that we are wanting to construct this separate from how we would deal with an onboarded company device.
The compliance policies will come more into play once we have agreed on the defined access policies for the BYOD devices.
Security Baselines & Patch Maintenance: Crucial to BYOD Device Management
An important part of the BYOD management will of course be around the hardening of the devices within the security baselines within Endpoint Management.
There are of course default baselines that are applied where applicable, but we may need to define our own explicit criteria for looking specifically at those devices.
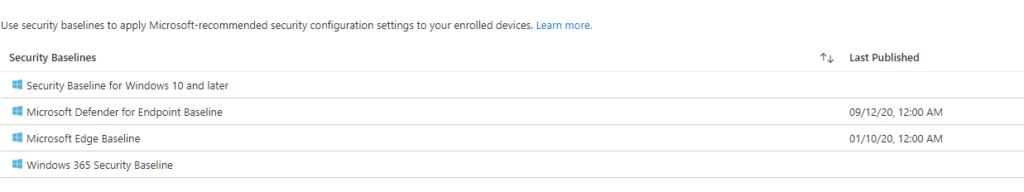
Figure 1.2 -Default Security Baselines Applied
The same can also be said for the update deployment through update rings and autopatch where applicable so this may be more geared towards Windows-based devices, but there will be focus and elements across the non-windows devices when it comes to the security aspect of BYOD management.
MAM Policies
Another point of interest is the development of MAM policies for when handling BYOD devices so that we are able to have a segment of control in regard to the configuration of the company-level applications as well as what data can be accessed as well as restricted when using these applications on company premises.
Next On Part 2
Part 2 is where we will dive further into the device enrolment section of this new series, this will not just focus on Windows Devices but across all mobile devices platforms also and should be a very in-depth planning part of the series for this area.
For comprehensive end-point management services, trust WME to streamline your BYOD ecosystem effectively.






