The corporate world is evolving fast. And with that, mobile devices are spreading everywhere. As we venture into the year 2024, they have already claimed a substantial 55% share of the total corporate device ecosystem.
You can say a seismic shift is underway and mobile phones have already become the dominant force. And, they are eclipsing the once-everywhere laptops.
Now, that means organizations need to carefully monitor the security of these devices. It has become extremely critical to scrutinize how users employ them to access and manipulate sensitive corporate data.
At the heart of this transformation lies the indispensable role of Microsoft Intune. In this comprehensive blog post, we’ll talk about everything related to Microsoft Intune. It’s going to be a full-fledged guide.
Let’s dive in.

What is Microsoft Intune?
Intune is a cloud-based tool for unified endpoint management (UEM) by Microsoft. Its main purpose is to help companies monitor and protect their mobile devices and data from a single pane.
Intune supports all popular types of OS i.e. Windows, Mac, iOS, Android, etc. With Intune, you can leverage the following:
✔ Device onboarding and configuration
✔ Policy Enforcement
✔ Mobile App Monitoring
✔ Security & Compliance Monitoring
✔ Enterprise Mobility
✔ Endpoint Privilege Management
As a quite powerful MDM and UEM tool, Intune helps organizations of all sizes that need to protect their moving devices.
Notably, its secondary features like interface, speed, etc. are also quite top-notch. It integrates seamlessly with other Microsoft products such as Azure Active Directory, Microsoft Defender for Endpoint, and especially Microsoft 365. All in all, Microsoft Intune is your go-to solution for all the endpoint management needs.
It’s worth noting that Microsoft Intune comes packaged with Microsoft 365. While some may compare it to the on-premises System Center Configuration Manager (SCCM), it’s important to note that the two tools are not equivalent.
Intune VS SCCM
SCCM is an on-premises solution and offers more extensive capabilities compared to Intune. However, with Intune getting more popular, SCCM is expected to go outdated in 6-7 years. However, so far, SCCM is far more powerful than Intune.
No doubt Azure AD offers capabilities to allow admins to enforce “Conditional Access (CA)” policies to access company resources. Now, if you combine Azure AD Conditional Access policies with Intune compliance policies, the power of MDM with Azure only skyrockets.
Microsoft Intune is an integral component of Microsoft’s Enterprise Mobility + Security (EMS) suite
EMS is a cloud-based suite of services that facilitates the management and protection of devices, apps, and data for organizations.
It can integrate seamlessly with Azure Active Directory (Azure AD), Microsoft 365, and Microsoft Defender for Endpoint.
Intune focuses on endpoint management within the EMS suite. Azure AD handles identity and access management. Whereas, Defender for Endpoint is responsible for security and threat protection.
That said, Microsoft Intune is also available as a standalone product.
Use cases of Microsoft Intune
☑ Install a new mobile app on all your employees’ devices.
☑ Enforce a policy that requires all devices to be encrypted.
☑ Remotely wipe a lost or stolen device.
☑ Monitor the compliance of devices with security and compliance policies.
Exclusive Features of Microsoft Intune
Remotely Enroll Devices And Troubleshoot Issues
There are many methods for device enrollment. User-driven enrollment, automatic enrollment, bulk enrollment, use any. During enrollment, the Intune agent is installed on the device. It then helps manage the device remotely. Intune can provide remote assistance to end-users, troubleshoot device issues, and resolve problems without requiring a physical presence.
Policy Configuration
Admins can create and configure custom MDM policies and enforce them with complete control and flexibility. These policies define how the devices should behave and what security settings they should comply with. Policies generally cover aspects i.e. device configuration, security settings, app management, and more.
Conditional Access
Intune works closely with Azure Active Directory (Azure AD) to enforce dependent access policies.
Conditional access allows you to control access to corporate resources based on different factors. For example, you can use factors like compliance status, compliance score, user identity, location, user behavior, device type, and whatnot.
You can deny access to devices that do not meet the specified criteria. You can also require them to go through necessary security checks, at any time.
App Management
Intune also allows organizations to manage and distribute applications to enrolled devices. Be it a company-owned device or a personal one, admins can deploy policies and sudden actions on them whenever they want.
Remote Wipe and Lock
This option allows you to restore the device to its factory status. All the corporate data will be deleted permanently from the device. You can use it in the event of a lost device. You can also use this feature when you are too conscious of your data’s security if an employee is just about to leave your organization. You can also enforce remote locking to prevent unauthorized access to the device.
Reporting & Monitoring
Intune offers comprehensive insights through reports and graphical representations of device and app status, policy compliance, and potential security vulnerabilities.
- Device Compliance Reports
- Device Inventory Reports
- Application Deployment Reports
- Security Reports
- Configuration Reports
- Software Update Reports
Security and Compliance
Intune comes with a wide range of security capabilities like encryption, threat protection, access control, automated response, etc. It ensures your precious data and apps stay safe and devices are always enrolled. You can define your custom compliance policies to be sure of your organization’s security status.
Mobile Device Management (MDM) & Mobile Application Management (MAM)
Get both MDM and MAM capabilities with Intune. Use MDM to manage the entire device whereas MAM focuses on managing and securing specific applications and their data on a device. The best thing is that MAM doesn’t impact personal user data while monitoring corporate data.
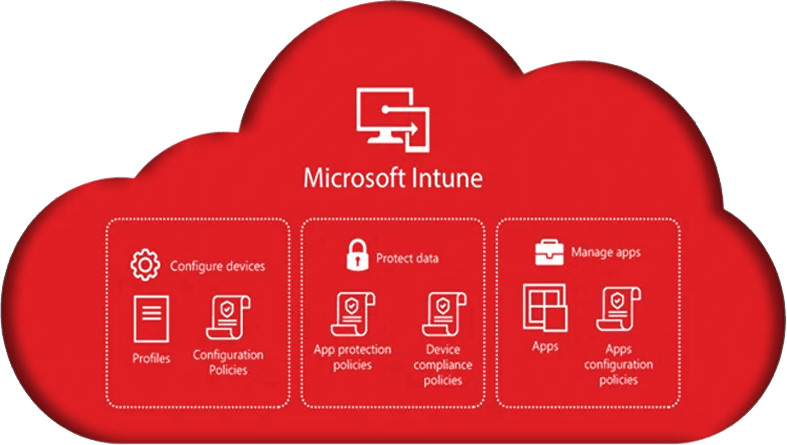
How to Get Started with Intune?
Microsoft Intune is compatible with the following Microsoft 365 licenses:
- Microsoft 365 E5
- Microsoft 365 E3
- Microsoft 365 Business Premium
- Microsoft 365 F1
- Microsoft 365 F3
- Microsoft 365 Enterprise Mobility + Security E5
- Microsoft 365 Enterprise Mobility + Security E3
- Microsoft Intune for Education
If you do not have one of these licenses, you can still use Intune by purchasing a separate license.
It supports the following OS & Browsers:
Operating systems:
- Windows 10 and 11
- macOS 11.0 and later
- iOS/iPad 13.0 and later
- Android 7.0 and later
- Linux with a GNOME graphical desktop environment (Ubuntu Desktop 22.04.1 LTS or later)
Browsers:
- Microsoft Edge (latest version)
- Safari (latest version, Mac only)
- Chrome (latest version)
- Firefox (latest version)
Follow these steps to sign up for Microsoft Intune:
- Go to the Microsoft Intune sign-up page.
- Enter your work or school email address and click Next.
- If you already have an M365 subscription, you will need to sign in to your account. If you do not have a subscription, you can create a new account or sign up for a free 30-day trial.
- After signing in, create an Intune tenant- a dedicated environment for your organization’s MDM.
- Now, you can enroll your devices.
There are multiple methods i.e. manual enrollment, device enrollment program (DEP), user-driven enrollment, etc.
Manual Enrollment:
Go to the Intune console and click Devices. Then, click Add and select Manual Enrollment.
Enter the device information and click Enroll.
Device Enrollment Program (DEP):
DEP allows you to automatically enroll Apple devices.
You need to register your organization with Apple and configure your Intune environment.
User-driven Enrollment:
Admins need to create an enrollment profile and distribute it to their users. Users will be able to enroll their devices on their own.
Assign Licenses to Your Users
- Go to the Intune console and click Users.
- Then, select the users and click Assign licenses.
How Does Intune Work?
- Now, after enrollment of the devices, Intune communicates with the cloud and receives policies.
- Then, every device applies the policies assigned to it.
- It reports its status to Intune regularly.
- You can use it to monitor the status of devices, deploy apps, manage security and compliance settings, and manage apps including:
✔ Internal apps
✔ Apps from the public app stores
✔ Line-of-business apps
To configure policies, go to the Intune console and click Policies. Then, click Create Policy and select the type of policy you want to create.
To monitor your devices, go to the Intune console and click Devices. Then, click the device you want to monitor and view its status.
19 Tips to Maximize the Benefits of Intune

Remember that the effectiveness of Intune depends on proper planning and configuration with your unique needs in mind.
Here are 19 vital, unique, and extremely useful tips to help you drive the best out of Intune:
- Enforce conditional access policies to control access to corporate resources based on conditions like device compliance, location, group, etc.
- Implement app protection policies and control actions like cut, copy, paste, etc. within intune-managed apps. You can enforce these rules regardless of the device’s status and it’s quite important for securing corporate data within your apps.
- Leverage Intune’s integration with Microsoft Defender for Endpoint to enhance device security.
- Set up Windows AutoPilot to simplify device provisioning. This streamlines the out-of-the-box experience for users.
- Set up Remote Wipe and Reset capabilities to protect sensitive data in the event of a lost or stolen device.
- Create custom configuration profiles to fine-tune device settings, including Wi-Fi, VPN, and email configurations.
- Identify the most critical security and configuration policies for your organization. Not all devices or apps may require the same level of management.
- Leverage automation and scripting tools i.e. PowerShell and Intune Graph API, to streamline repetitive tasks.
- Encourage self-service capabilities, like app installation through the Company Portal, to offload IT support tasks.
- Make the most of Intune’s reporting and analytics features to gain insights into device compliance, security incidents, app usage, etc.
- Organize devices into custom categories based on user roles, departments, or device types. This allows you to apply policies to specific groups rather than managing all devices uniformly.
- Maintain separate testing and staging environments to evaluate policy changes and app deployments before implementing them in the production environment.
- Implement RBAC to delegate administrative responsibilities.
- Create compliance baselines for devices to ensure they adhere to your organization’s security standards. These baselines can be customized to meet specific requirements and automatically trigger remediation actions for non-compliant devices.
- Document your Intune configurations and processes to facilitate knowledge sharing and troubleshooting.
- Monitor resource utilization within Intune i.e. licensing and storage. Optimize your license allocation based on actual device usage to avoid unnecessary costs.
- Establish a feedback loop with end-users and IT staff to gather input on the usability and effectiveness of Intune policies and configurations.
- Develop and document emergency response plans for security incidents and policy failures. This ensures you can respond swiftly to critical issues without wasting time during a crisis.
- Conduct periodic audits and reviews of your Intune setup to identify areas for improvement and security gaps.
For a more detailed explanation, see the top 7 Intune best practices.
Cost Structure of Microsoft Intune
| Plan | Price per user per month | Included features | |
| 1 | Microsoft Intune Plan 1 | Included with Microsoft 365 E3, E5, F1, F3, Enterprise Mobility + Security E3 and E5, and Business Premium plans. | Cross-platform endpoint management, built-in endpoint security, mobile application management, and endpoint analytics. |
| 2 | Microsoft Intune Plan 2 | $6 per user per month | All features of Microsoft Intune Plan 1, plus advanced endpoint management capabilities such as configuration profiles, compliance policies, and remote actions. |
| 3 | Microsoft Intune Suite | $12 per user per month | All features of Microsoft Intune Plan 2, plus mission-critical advanced endpoint management and security solutions such as Microsoft Defender for Endpoint and Microsoft Threat Protection. |
| 4 | Device-only licenses | $2 per device per month | For managing devices that aren’t affiliated with specific users. Available for Windows, macOS, iOS, Android, and Linux devices. |
- Overage charges may apply if you exceed the number of device licenses included in your plan.
- Support costs may apply if you need assistance from Microsoft support.
- Discounts are available for non-profit organizations and educational institutions.
- Volume discounts are available for organizations with more than 500 users.
Alternatives to Microsoft Intune
NinjaOne
NinjaOne and Intune are both robust endpoint management solutions, but they cater to different MDM needs.
NinjaOne is not a replacement for a Remote Monitoring Solution. Whereas, Intune can work in harmony with top-notch Remote Monitoring tools like NinjaOne to provide a comprehensive MDM experience that’s designed for Managed Services Providers.
NinjaOne is known for its user-friendly interface and comprehensive monitoring capabilities. It offers detailed insights into endpoint performance and security. On the other hand, Intune has its unique advantage as it’s part of Microsoft’s ecosystem. It seamlessly integrates with all Microsoft services and can help you to expand your remote network without any hassle.
Basically, Intune is matchless in its MDM effectiveness in enterprise environments whereas NinjaOne excels at providing coverage of everything connected in a network for an MSP.
Manage Engine Endpoint Central
ManageEngine Endpoint Central is cost-effective but certainly not at the cost of the quality of its service. It comes with a really wide range of features that cover everything from MSD to security to remote wipe capabilities.
Its endpoint security and asset management are the two most praised features that are getting personalized reviews on the Internet. It also offers dependable patch management for applications. But it lags behind Intune in its integration capabilities with Microsoft 365 and Azure AD. Also, Intune’s application deployment capabilities and conditional access policies make it a priority for many organizations, especially those invested deeply in the Microsoft ecosystem.
IBM Security MaaS360
IBM Security MaaS360 has AI-driven security & MDM-related insights as its most unique selling point. It’s also recognized for its robust security protocols and support for a wide range of devices and OS.
Mobile expense management, Bring Your Own Device (BYOD) Support, secure content collaboration, integration with IBM security, containerization, advanced reporting and analytics, geofencing and compliance policies, etc.
Ivanti Unified Endpoint Manager
Ivanti Unified Endpoint Manager offers a holistic approach to endpoint management via implementing zero-trust strategies across your enterprise. It provides dependable device control features, patch management, security, and whatnot. It also provides extensive support for nearly all the popular operating systems. Intune, on the other hand, builds its reputation on its ability to manage Windows-specific applications.
ESET PROTECT Advanced
ESET PROTECT Advanced offers quality endpoint management features but it has some killer antivirus and anti-malware solutions. This is its unique selling point and even Intune doesn’t surpass in its anti-malware capabilities.
It comes with splendid threat detection and mitigation tools whereas Intune’s security features are just a reflection of the security profile of Microsoft 365- which is fine, if not too hot to handle.
ESET also offers the latest threat intelligence and application control features. Its integration with Windows Defender ATP enhances its threat detection capabilities and makes it such a valuable package for those in need of advanced security measures.
All in all, the choice between these MDM solutions depends solely on your specific organizational needs and your tech ecosystem. Sometimes, your biggest constraint is budget. Sometimes, your utmost need is the perfect integration of Intune with your infrastructure. Sometimes you want user-level ease and, at times, the most sought-after feature is endpoint security. It really depends on what you need and what particular features your team feels can provide them with the best solutions.
Intune, however, is the market leader for a reason. For many organizations today, it’s getting the acceptance of a level you expect from a top-level global product. Despite some concerns over its intuitiveness and complex configuration process, companies have been showing trust in Intune for a long time now.
Even, experts are predicting that Intune will turn SCCM obsolete in a matter of few years. Let’s wait and watch.
Explore Application Group Deployment using SCCM
Wrapping it Up:
Intune is like the Swiss Army knife of modern device management. It offers a plethora of tools to help organizations navigate the demands of mobile device security.
We’ve taken a deep dive into this MDM tool in this long guide. We saw how to set up policies, protect your data, and keep devices running smoothly.
It’s not just a collection of features, it’s a smart, flexible solution that allows your teams to customize their approach to security and productivity quite flexibly.
But remember, Intune isn’t a one-size-fits-all deal. It’s all about configuring it to meet your organization’s unique needs and schedules. By doing so, you can make Intune work wonders for your team.
WME Intune Services
WME can enhance end-user device capabilities & speed up your business excellence. Your business might be at the forefront of a subtle opportunity you feel you can’t grab without external help. We also provide you with pre-sales professional help and assist you with choosing your best Intune options.
For all the clients seeking a Professional or Managed Intune service, you can bank on our experts who have gathered a collective experience of decades so far.
Even, if you can’t decide between different vendors or services, we’ve got you covered. We’ll also help you with diverse services such as Microsoft 365, Teams, SharePoint, and whatnot.
Empower your company to take your It game to the next level of brilliance. Partner with WME.









