With its AI-powered productivity-enhancing capabilities, Microsoft Copilot has emerged as a game-changer for employees, particularly for organizations using Microsoft 365.
But before you hit the enable button and dive headfirst into Copilot’s world, it’s crucial to consider some factors. When integrated with Micorosft 365, Copilot deployment demands some solid tenant readiness evaluation and permission setup.
This blog post delves into the top 3 key considerations, focusing on navigating the permission landscape. We’ll explore how Copilot interacts with your data, the potential security implications, and strategies for ensuring responsible use.
By understanding these factors, you can efficiently harness the power of Copilot for Microsoft 365.

3 Things to Consider Before You Enable Microsoft Copilot
While Copilot can boost productivity, it’s not a magic bullet. Before you start using it with Microsoft 365, here are 3 key considerations.
1. Streamlining Microsoft 365 Label Management
Sensitivity labels in Microsoft 365 protect data. With the addition of auto-labelling, users no longer need to label the data manually since the feature applies the labelling policies automatically.
However, all content authored by Copilot should be reviewed to ensure it follows the prescribed labelling guidelines and safeguards data.
2. Best Practices for Data Protection
Effective data protection includes, but is not limited to:
- Access assignments on a need-to-know basis,
- Application of the least privilege principle,
- Data categorized by its sensitivity,
- Access Control Lists (ACLs),
- User identity authentication,
- And data encryption.
You also need to keep detailed activity logs and do data segmentation and periodic access reviews that are excessive and unnecessary.
Clear access and data guidelines should be set to be enforced and communicated to all parties involved.
3. Prerequisites To Deploy Microsoft Copilot Include:
- Microsoft Azure subscription
- Entra IDAccount
- OneDrive for the storage of data
- Updated Outlook for both Windows and Mac
- A properly configured MS Teams
- Activated “Loop Function” in your Microsoft tenant
- Adherence to Best Practices of the Network
- Microsoft 365 application
- Additionally, with Copilot in use, an add-on license is available only with Microsoft 365 Business Premium and M365 Business Standard.
Let’s understand these 3 Copilot Considerations in detail…
1. Streamlining Office Label Management
A Deep Dive into Copilot’s Impact on M365 Labels…
Perhaps the most prominent way Microsoft Copilot integrates into Microsoft 365 applications—like Word and Excel—is by driving massive gains in workflow efficiency.
The ease it brings with auto labelling is just incomparable. But, there are some security concerns as well.
Let’s dive deeper into what benefits this auto labelling can provide and what considerations are needed.
Technical Underpinnings of Auto-Labelling
Machine learning: Copilot’s auto-labeling is based on machine learning algorithms trained over huge sets of labeled documents.
This is achieved through ML algorithms, which scan the content of documents to find keywords, phrases, and patterns that match certain sensitivity levels.
Sensitivity Policies: Microsoft 365 enables an organization to establish sensitivity policies. The policy states the criteria under which content in the document is to be classified.
For example, “Confidential,” “Internal,” and “Public.”
When these policies exist, Copilot assigns the correct label automatically.
Integration with Azure Information Protection (AIP)
For advanced security, Copilot integrates with Azure Information Protection (AIP).
AIP imparts an organization with granular access controls of documents based on their sensitivity labels. This ensures that only authorized persons can view the respective information.
Benefits of Auto-labeling with Copilot
Improved Efficiency: Auto-labeling does not require manual effort from the user to allocate labels.
It is actually of great help for organizations that need to maintain a large number of documents.
Improved Consistency: Manual labeling is subjective and opens up the process to human error.
With a machine learning approach, Copilot ensures that all the labels are consistent across the documents, hence reducing inconsistencies that may cause a violation of data security policies.

Streamlined Workflows: Auto-labeling seamlessly fits into the existing workflows. So, it allows users to concentrate on generating content, leaving all the label-juggling tasks for Copilot to manage behind the scenes.
2. Data protection
Build a Fortress Around Your Sensitive Information…
Data protection lies at the heart of information security. It includes a diverse set of strategies that help you secure valuable data for your organization from getting damaged and lost and unauthorized access, misuse, disclosure, disruption, modification, or destruction.
Here are some of the most important best practices with some technical considerations.
The Pillars of Data Protection: Before Deploying Copilot for Microsoft 365
1. Principle of Least Privilege (POLP)
POLP makes sure the least level of permissions and privileges is assigned to users. That means, only to an extent that enables them to do their jobs.
This is based on the goal that even a compromised user’s credentials should cause no damage.
Technically, this would be realized through role-based access control (RBAC) systems that assign permissions based on pre-defined user roles.
2. Access Control Lists (ACLs)
These specify who can access what data resources and to what level—reading, writing, deleting, etc. They greatly help in managing Active Directory in Windows environments and other similar directory services of other OSs smoothly.
3. Data Classification & Categorization by Sensitivity Levels
As described above, not all data elements are equally sensitive.
So, organizations have to classify and categorize their data according to its sensitivity (such as public, internal, and confidential) into the right sets.
This is where the Data Loss Prevention (DLP) solutions come into the picture. The sensitive data should be restricted and checked by putting DLP solutions into place, which are based on predefined policies.
4. User Identity Authentication
This is a process that verifies the identity of a user before providing access. Multi-factor Authentication (MFA) takes the process way above mere passwords by adding one more step: authenticating a code from a phone app (there are other, more sophisticated ways as well) to enhance the level of security.
5. Data Encryption
Encryption is the conversion of data, via mathematical algorithms, into unreadable text. Its purpose is to keep the data unretrievable when it’s transmitted to storage and anywhere else. Only a proper decryption key can help restore it to its original, usable form.
When using Copilot for Microsoft 365, data storage facilities and all transmissions should only be on an encrypted basis. An organization can use encryption solutions like BitLocker for the disk drives and Secure Sockets Layer (SSL) / Transport Layer Security (TLS) protocols for network communication.
Communication: The Framework of Compliance
Data security is ultimately a technical and cultural challenge.
It must be implemented through clear and concise policies that are well-communicated to all users. Policies related to effective data security should be clearly communicated to employees via regular security training to make them aware of the threats and best practices for data management.
By deploying these best practices and leveraging the right technology solutions alongside Copilot, your organization can surely establish a sound data protection architecture that further reduces the risks of data breaches.
This way, you can comply with all data privacy regulations and ensure the protection of the confidentiality, integrity, and availability of valuable information assets.
3. Prerequisite Essentials for Deployment
Gearing Up for Copilot…
Microsoft Copilot may add value to your Microsoft 365 but before you get started, there are key things you need to have in place for its successful deployment.
Let’s break it down:
Identity & Authentication
Microsoft Entra ID (Azure AD): Copilot uses Entra ID (previously Azure Active Directory) for your user authentication and authorization services.
This service allows you to manage your users’ identity and access to Microsoft Cloud applications in your organization. A user who is to use Copilot must have an active Entra ID account.
Microsoft 365 Apps: This is the key productivity suite, including the likes of Word, Excel, PowerPoint, and others. Copilot will require a subscription to Microsoft 365 that includes this core suite of applications.
OneDrive: This is the main storage used by Copilot. It includes stored user data, helps with sharing collaboration features, and provides the possibility to access documents from any device. Hence, each user has to make sure that they have an active OneDrive account.
Microsoft Loop (Optional): When turned on in your Microsoft tenant, this will allow you to fully leverage the collaboration superpowers of Loop from in Copilot. Loop allows you to co-author documents in real-time while working within a fluid environment that transitions seamlessly from other Microsoft 365 apps.

Code Quality & Accuracy with Copilot
What Microsoft Copilot promises is a game-changer for developers. However, the way it works puts forward a critical question.
Is the quality and accuracy of its suggestions dependable?
Leverage Copilot’s Strengths While Preventing Risks
Maintain a Critical Eye: Treat suggestions from Copilot as drafts, not the finished product, and always carefully look at the code being generated. Still, you may not have a solid understanding of coding principles, but you can recognize stumbling points and adjust the suggestions to suit your needs.
Test, test, test: Be willing for unrelenting testing. Do not just take Copilot’s suggestion. Even if it looks perfect, it probably is not. Test it again and again until you are sure it is doing what you want and not introducing any surprises.
Copilot is a valuable tool for developers but it’s not a silver bullet. You should understand possible pitfalls and be critical in your thinking to exploit Copilot’s potential to write better and faster code. In the end, you will be responsible for ensuring quality code.
Copilot for Microsoft 365 Limitations
| Application | Limitations / Challenges |
| Word | – Lacks nuanced understanding of legal/technical jargon, leading to errors in sophisticated documents. – Struggles with complex formatting tasks like multi-level lists, intricate table designs, etc. |
| Excel | – Does not handle advanced financial modeling like Monte Carlo simulations, effectively. – Struggles with custom VBA macros, complex pivot table configurations. |
| PowerPoint | – Limited capability generating multimedia-rich presentations. – Inability to create detailed custom animations/transitions. |
| Outlook | – Inaccurate suggestions for email responses in highly specialized fields. – Struggles with complex scheduling, calendar tasks across time zones. – Limited ability to filter/prioritize emails based on nuanced preferences. |
| Teams | – Limited real-time contextual understanding. For example, during live meetings. – Inability to integrate seamlessly with custom third-party apps in Teams. |
| OneNote | – Inaccurate conversion of handwritten notes with complex diagrams to digital text. |
| SharePoint | – Challenges in managing complex site structures and custom workflows. – Inability to provide advanced search and indexing for specialized content. |
| Planner | – Struggles with integrating detailed project plans with other PM tools. |
| Dynamics 365 | – Limited in automating complex business workflows. – Inaccurate insights for industry-specific CRM requirements. |
Conclusion
Microsoft Copilot is a dream come true for employers looking to get the most out of their employees. Developers, writers, marketers, data analysts, and whatnot, are now able to soar through their productivity experience with Copilot’s backing.
However, with great power comes great responsibility.
So, understand the permissions required for Copilot when you are integrating it with Microsoft 365. Think critically about DLP policies and tenant readiness, and how to use Copilot to skyrocket the productivity of your organisation while bolstering its security.
What Is Microsoft Security Copilot? A Full-Fledged Guide
Remember, for programming and code, you are the ultimate evaluator of your work. So, the ultimate responsibility for Coploit utilization and its security lies with you. Always implement the security best practices while deploying Copilot for Microsoft 365.
Unleash the Full Potential of Copilot for Microsoft 365
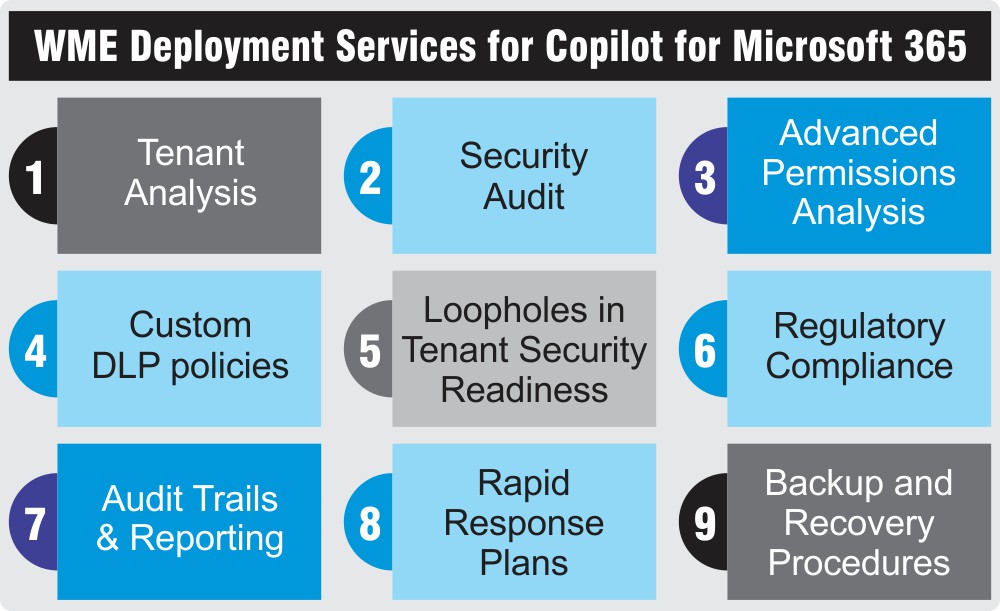
Windows Management Experts
All in all, when you grant partners access to Microsoft Copilot for Security to us, you partner for peace of mind. We will enable your MSSP to get the most from Copilit for more effective and efficient security, allowing you to carry on with your business without fear. Are you ready to collaborate with us with Copilot for Security?
We are now a Microsoft Solutions Partner for:
✓ Data & AI
✓ Digital and App Innovation
✓ Infrastructure
✓ Security
The Solutions Partner badge highlights WME’s excellence and commitment. Microsoft’s thorough evaluation ensures we’re skilled, deliver successful projects, and prioritize security over everything. This positions WME in a global tech community, ready to innovate on the cloud for your evolving business needs.







