Data breaches and shadowy cyber threats are at every turn of the digital landscape. Be sure, cybersecurity compliance measures are no minor matters.
Picture your company as a fortress and your sensitive data as its most prized treasure. The integrity of this fortress relies not just on sturdy walls but on a vigilant and proactive defense strategy.
Cybersecurity compliance is that defense, allowing your business to respond to threats and eliminate them. This article discusses the kind of data that must be protected, the compelling reasons to maintain a stringent cybersecurity posture, and provides a helpful checklist to evaluate your present compliance posture.
Let’s dive in…
Types of Data Subjected to Cybersecurity Compliance
Personal Identifiable Information (PII)
Address, name, phone number, social security number, email address, etc.
Protected Health Information (PHI)
Health records, treatment history, insurance information, other health-related information, etc.
Financial Information
Credit card number, bank account info, transaction history, tax information, etc.
Intellectual Property
Patents, copyrights, trade secrets, proprietary algorithms, business strategies, etc.
Operational Data
Internal communications, business processes, strategic plans, among other info.
Payment Card Information (PCI)
Credit and debit card number, cardholder information, transaction records.
Employee Data
HR records, payroll details, performance appraisals, past work history, etc.
Customer Data
Purchase history, contact information, preferences, feedback, etc.
Confidential Business Information
Contracts, business agreements, non-disclosure agreements (NDAs), financial statements, etc.
Supplier and Partner Information
Contracts, payment details, communication records with suppliers/partners, etc.
Government and Regulatory Data
Compliance reports, audit observations, regulatory submissions, etc.
All these types of data mandate stringent security practices to comply with the regulations discussed ahead.
Check Out: Enhancing IT Security and Compliance: A CPA’s Guide to Advising Clients
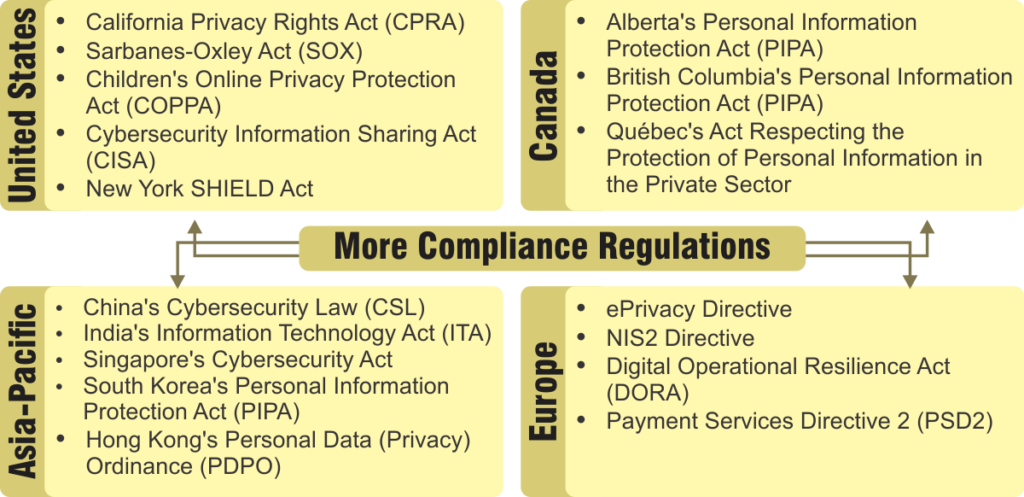
Data Protection Regulations Around the World
United States
HIPAA: Protects sensitive patient info in healthcare.
GLBA: Protects consumer financial info held by financial institutions.
FISMA: Ensures information security in federal agencies and help by contractors.
CCPA: Empowers California residents with control over their personal data.
Canada
PIPEDA: Governs how private businesses collect and disclose personal info.
Europe
GDPR: The gold standard for data privacy as it grants EU residents extensive rights over their data.
NIS Directive: Focuses on cybersecurity measures for essential services/digital providers.
Asia-Pacific
Japan (APPI): Regulates the collection and handling of personal data.
Australia (Privacy Act & APPs): Sets guidelines for handling personal info by government/private entities.
Key Implications
Organizations operating globally need to ensure they comply with a complex set of global regulations. These regulations generally require:
Check Out: NERC CIP Compliance with Microsoft 365 and Azure
Transparency: Be upfront about data collection.
Consent: Obtain clear, informed consent for data processing.
Security: Implement appropriate measures to protect personal information.
Individual Rights: Allow individuals to access and delete their data.
Breach Notification: Report data breaches to authoritie/affected individuals.
Staying Compliant
Understanding these regulations is crucial for businesses to operate compliantly and minimize risks associated with data breaches and hefty fines.
Benefits of Cybersecurity Compliance for the Corporate Sector
Strong cyber security compliance is a win-win for your business. It protects sensitive information and builds customer trust. Plus, it saves money by preventing costly attacks and streamlines security procedures.
You can mitigate the danger of Internet crime and financial loss while protecting your business name. Compliance simplifies security management and positions your business differently in the marketplace, all while averting information compromise costs.
The Consequences of Noncompliance in Business
The stakes are high for corporate institutions that neglect regulatory compliance. Failure to meet industry standards can result in hefty fines, reputational damage, and even legal repercussions. Also, non-compliance can disrupt your business OPs, as data breaches can lead to costly downtime. If your corporation prioritizes compliance with cybersecurity regulations, you can protect your customers’ trust and ensure smooth operations while complying with legal essentials.
Check Out WME’s Cybersecurity & Compliance Staffing Service
The Role Of Cyber Security & Compliance Services Providers
Let’s bridge the gap between the technical aspects of compliance and its impact on your business.
An established cybersecurity and compliance professional or managed service provider is your trusted advisor in this journey. They possess an in-depth understanding of regulations and compliance knowledge. They help you eliminate the compliance-related complexity for your business.
Imagine a customized roadmap – they’ll assess your specific vulnerabilities and provide custom advice for your specific needs. In fact, they’ll guide your internal teams every step of the way. So, this translates to implementing the most effective controls while minimizing disruptions. Ultimately, you can focus on what truly matters – your core business and compliance goals are also achieved.
Conclusion
The importance of Cybersecurity regulations and standards can’t be over-emphasized. The United States, Canada, Europe, and Asia-Pacific are the regions where holistic frameworks have been set in place to combat the changing cybersecurity landscape.
The corporate world needs to keep track of the regulations and maintain rigorous security standards. They need to abide by a culture of compliance to protect their assets. Non-compliance can invite enormous financial penalties, which explicitly sets the stage for the importance of compliance.
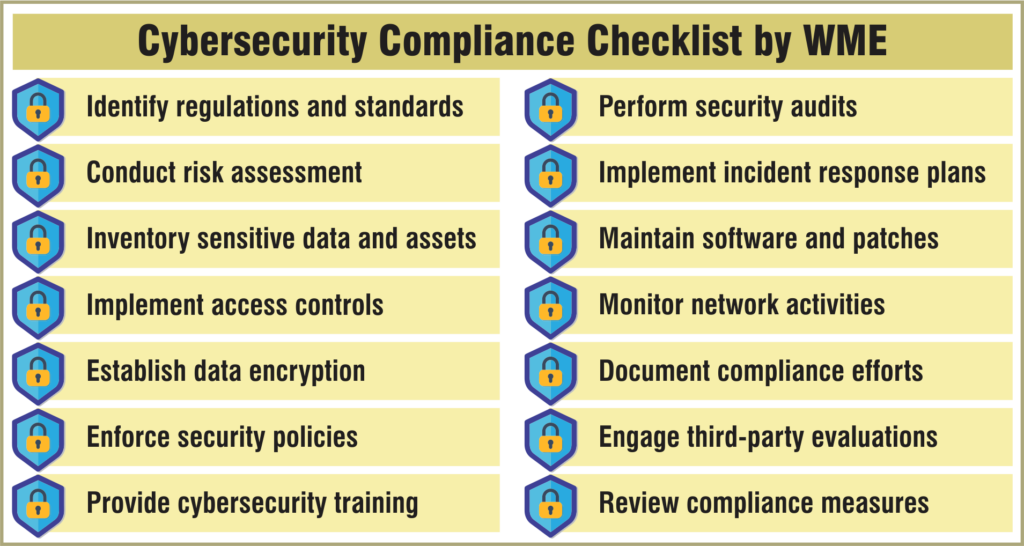
Empower Your Business with Confidence: Achieve Robust Cybersecurity Compliance
At Windows Management Experts (WME), we understand the challenges of today’s difficult compliance issues. Our seasoned professionals can help you achieve a handsome compliance score and protect your company from getting caught by wild fines and reputational damage.
Partner with WME for Your Cybersecurity Compliance Needs
✓Simplify Compliance
✓Rigorous Security Posture
✓Empower Your Team
✓Prepare for the Unexpected
Windows Management Experts
Now A Microsoft Solutions Partner for:
✓ Data & AI
✓ Digital and App Innovation
✓ Infrastructure
✓ Security
The Solutions Partner badge highlights WME’s excellence and commitment. Microsoft’s thorough evaluation ensures we’re skilled, deliver successful projects, and prioritize security over everything. This positions WME in a global tech community, ready to innovate on the cloud for your evolving business needs.
Don’t wait until it’s too late.
Contact WME today at sales@winmgmtexperts.com to discuss your unique compliance needs.







